Build Events in Splunk Related to Which of the Following
You can search for related events and group them into one single event called a transaction sometimes referred to as a session. Root event datasets are typically defined by a simple constraint.

Manage Event Storms With Splunk Itsi Event Analytics Splunk
Different events from the same source and the same host.
. When data is added to your Splunk instance the indexer looks for segments in the data. As far as I can tell from how to calculate duration between two events Splunk one way to do this is to use strptime to convert those time fields into time values and then determine their difference. 18 How can you extract fields.
For example status 600 and sourcetypeaccess_ OR sourcetypeiis are possible event dataset definitions. Kubernetes which refers to the Greek word for helm or helmsman is an open source software that performs container orchestration. 17 Explain default fields for an event in Splunk.
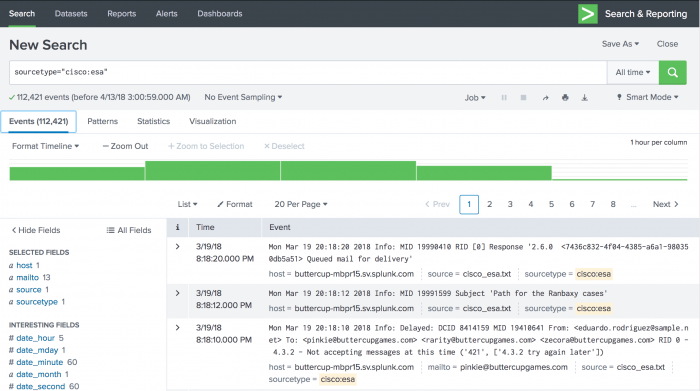
1 host 2 source 3 source type 4 index and 5 timestamp. Track a series of related events which may come from separate IT systems and data sources together as a single transaction. I happened to check my logs for this problem today and found 81 events in the last 24 hours.
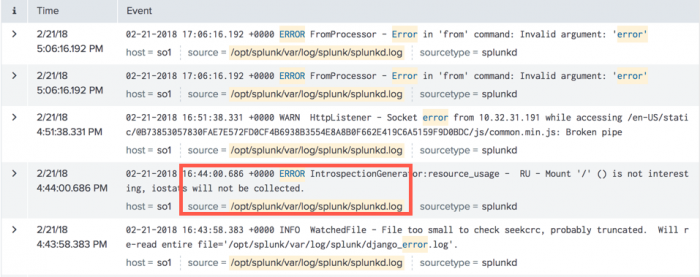
The data itself comes from Splunk indexes but ITSI only focuses on a subset of all Splunk Enterprise data. See more follow up resources on our community. Specifies a regex that determines how the raw text stream is broken into initial events before line merging takes place.
Please correct me if Im wrong. Splunk software supports event correlations using time and geographic location transactions sub-searches field lookups and joins. Tune into the Tech Talk to learn how to a build model with your Splunk data using machine learning.
Event segmentation and searching. And how to use the RWI zoom related apps add-ons on Splunkbase. The results will be the most recent events by default because splunk returns events in time order unless explicitly sorted.
However the time of the events was already parsed when importing the data as seen from the built-in _time field so this seems inefficient to me. Below is how my log prints. This documentation applies to the following versions of Splunk.
Kubernetes frequently shortened to k8s can manage scale and deploy containerized applications like Docker. Build resilience to meet todays unpredictable business challenges. Identify and group events into transactions.
Adding a new event type in Settings. After data is ingested into ITSI from multiple data sources events proceed through the following workflow. Entire businesses and applications are built on open APIs relying on the ability to pass data back and forth between.
By the way to provide a minor update to the first post the network traffic data model build has completed and is at 100. The more interesting case is fixed duration queries. Splunk ITSI Event Analytics is designed to make event storms manageable and actionable.
I still have the issue. I am new to Splunk. Hence i would require some support to build search query.
An event correlation tool can map and contextualize the data it ingests from infrastructure sources to identify suspicious patterns in real time. Defaults to rn meaning data is broken into an event for each line delimited by any number of carriage return or newline. EY Turns Data into Doing.
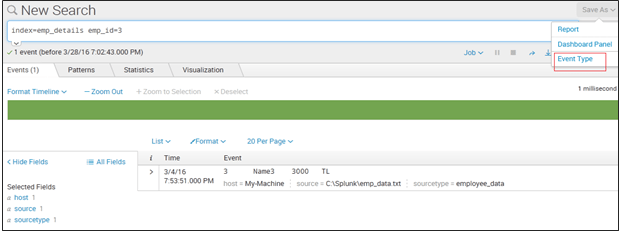
All events appear at random time intervals with an average of 15 events for each occurrence. Select Settings Event Types. Optional Change the Destination App value to the correct app for the event type if it is not your current app context.
Splunk Events Join us at an event near you to gain new skills expand your network and connect with the Splunk community. Kubernetes users can define what kind of container architecture they want and the software. Not sure if the issue might be the fact that ServiceNow uses GMT and therefore all the tickets have the dv_opened_at and dv_closed_at field in terms of GMT and the _time field is the local time which in my case is EST.
This sets SHOULD_LINEMERGE false and LINE_BREAKER to the user-provided regular expression. Provide a unique Name for the event type. Enter the Search String for the event type.
APIs give DevOps professionals instructions about how to interact with services and can be used to connect data among different systems. There are 5 default fields which are barcoded with every event into Splunk. In order to extract fields from either sidebar event lists or the settings menu using UI.
Data is segmented by separating terms into smaller pieces first with major breakers and then with minor breakersThese. With the help of event correlation an intrusion detection system could recognize these related events as a potential cyberattack and alert the appropriate team. Different events from different sources from the same host.
Focus on high fidelity threats to your environment with Event Sequencing in Splunk Enterprise Security and accelerate time to investigate and respond to incidents. Hi Im trying to build a query to get the count of opened and resolved incidents every hour in a day but the numbers are not tallying. 181 xxxx-xx-xx xxxxxx INFO lots of textRITM1234FAILED BECAUSE ROOT.
An API is a set of programming instructions and standards for accessing a web-based software application or service. This constraint is what an experienced Splunk user might think of as the first portion of a search before the pipe character commands and arguments are applied. This search consistently returns a specific kind of event.
Using Events Lists Splunk Documentation

Identify Event Patterns With The Patterns Tab Splunk Documentation
Knowledge Objects Splunk Events Event Types And Tags By Aayushi Johari Edureka Medium
Comments
Post a Comment